Don’t let data requests be your next vulnerability
Data requests are the new attack vector that threat actors exploit to get access to your company’s most sensitive data. Stay one step ahead and stop sophisticated attacks before they succeed.



CISO Priorities and Risks
Bad actors use legitimate law enforcement credentials and domains to bypass your security perimeter and socially engineer companies into handing over their most sensitive data.
Your experts waste hours coordinating manual requests across departments. Critical threat hunting and prevention work gets delayed.
Your teams rely on email to process data requests, making social engineering all too easy. Data requests often go unverified and impersonators aren’t caught until data productions have already occurred.
Complex regulations demand complete visibility. Current tools leave dangerous gaps in your security documentation.
Secure your third-party data requests

Active Threat Prevention
Convert every data request into actionable security intelligence. Block sophisticated impersonation attempts with built-in verification systems.


Secure, Encrypted Portal
Ensure every communication and data production is sent via a secure, encrypted portal, versus an insecure, unencrypted, and fragile email.
Enterprise-grade security and compliance
Certified across the frameworks that matter most to your legal, compliance, and security teams.

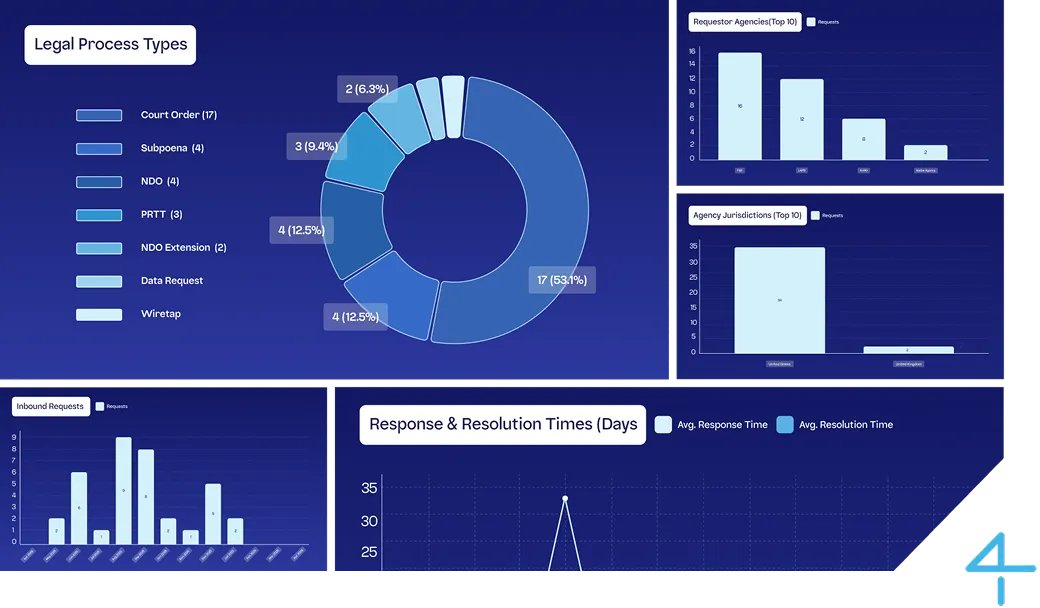
Security Analytics
Measure risk reduction in real-time. Show concrete security improvements with data-driven reporting.
Why the world's most trusted Security Leaders use Kodex for data requests

85%
less time spent on manual processes
1M$+
saved in compliance violations
5K+
law enforcement impersonators blocked
Stay ahead of bad actors.
Protect your company from threat actors using data requests to hack into your company’s most valuable data.


.svg)



